Permission System
DataForeman uses a flexible, granular permission system to control user access to features and operations.
Overview
Permissions are managed through the web interface:
- Feature-based: Control access to specific features
- Operation-based: Separate Create, Read, Update, Delete permissions
- User-specific: Assign permissions individually per user
- Admin override: Admin users have full access automatically
Accessing Permission Management
- Login as administrator
- Click user icon → Users in top-right corner
- Select user from list
- Scroll to Permissions section
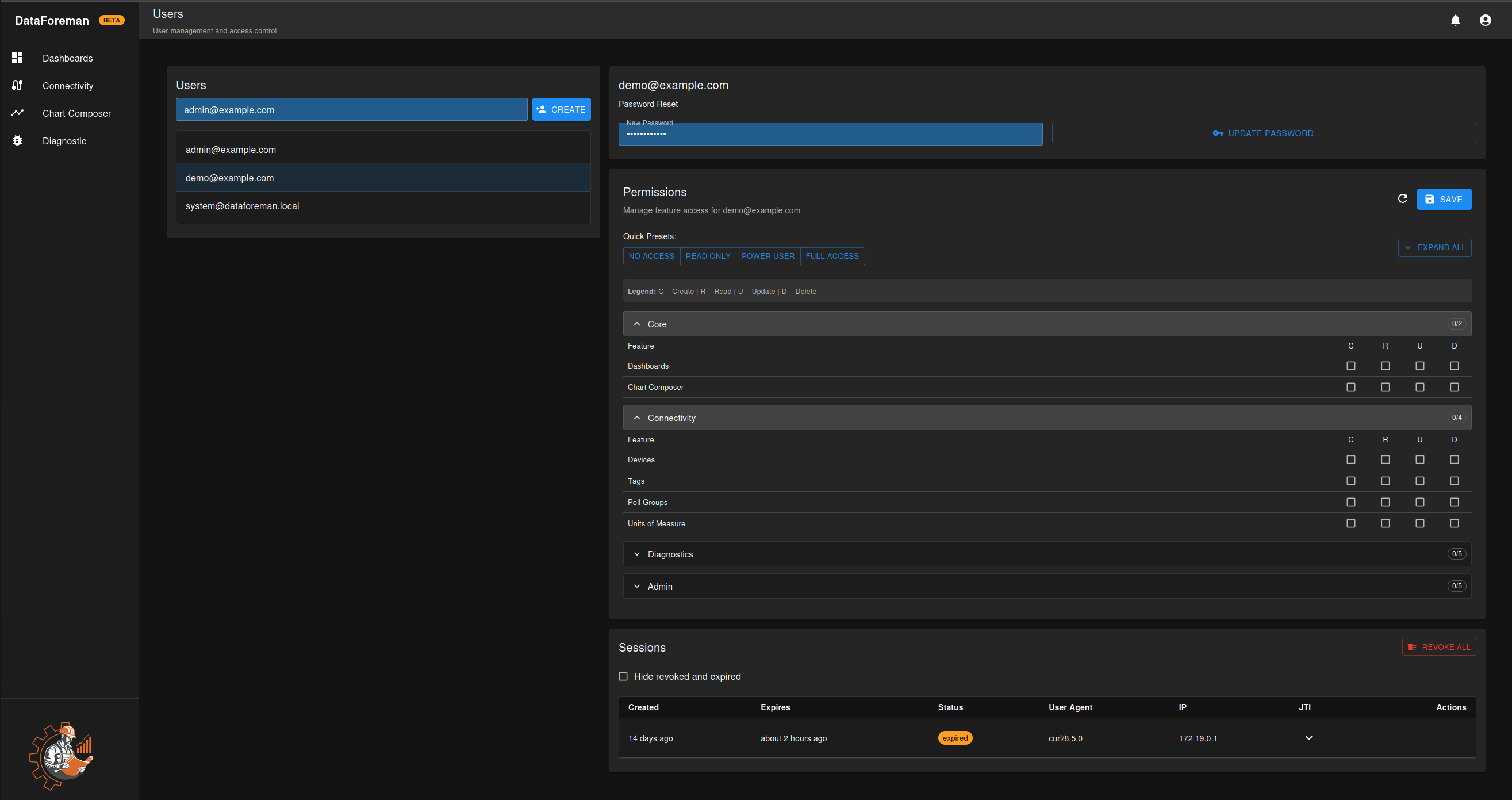
Permission Structure
Each feature has four operations:
| Operation | Symbol | Description |
|---|---|---|
| Create | C | Add new items (dashboards, connections, tags) |
| Read | R | View existing items and data |
| Update | U | Modify existing items |
| Delete | D | Remove items |
Permission Categories
Core Features
- Dashboards: Dashboard and chart management
- Chart Composer: Time-series data visualization
Connectivity Features
- Devices: Device connections (OPC UA, EIP, S7)
- Tags: Tag metadata and configuration
- Poll Groups: Polling rate management
- Units: Engineering units and conversions
Diagnostic Features
- System: System diagnostics and monitoring
- Capacity: Database and storage capacity
- Logs: System and service logs
- Network: Network diagnostics
Admin Features
- User Management: Create and manage user accounts
- Permissions: Configure user permissions
- Jobs: Background job management
- Configuration: System configuration
Quick Presets
Apply common permission templates instantly:
| Preset | Permissions | Best For |
|---|---|---|
| No Access | None | Disable user temporarily |
| Read Only | Read on all features | Reporting, viewing |
| Power User | Create, Read, Update | Operators, engineers |
| Full Access | All permissions | Trusted administrators |
To apply preset:
- Select user
- Click desired preset button
- Click Save button
- User must logout/login to see changes
Configuring Individual Permissions
Manual Configuration
- Select user from list
- In Permissions section, expand category
- Check/uncheck boxes for each operation
- Click Save button
Example: Allow dashboard creation only:
- Core → Dashboards: ✓ Create, ✓ Read
- Leave Update and Delete unchecked
Permission Categories
Click category name to expand/collapse:
- Core: Dashboard and chart features
- Connectivity: Device and tag management
- Diagnostics: System monitoring tools
- Admin: Administrative functions
Admin User Protection
Admin users have special protection:
- Permissions cannot be modified
- Prevents accidental lockout
- Always have full system access
- Identified by email (admin@example.com)
Note: Admin account permissions are fixed to ensure system access.
Permission Enforcement
UI Level
Interface adapts to user permissions:
- Hidden buttons for unauthorized operations
- Disabled features user cannot access
- Menu items reflect permitted features
API Level
All requests checked automatically:
- JWT token verified
- Permissions validated
- Unauthorized requests rejected
Best Practices
Least Privilege Principle
- Give users minimum permissions needed
- Start with Read Only preset
- Add permissions as needed
- Review permissions regularly
Regular Reviews
- Audit user permissions quarterly
- Remove permissions from inactive users
- Update when job roles change
- Document permission decisions
Separation of Duties
- Don’t give everyone admin access
- Separate configuration from operation
- Limit who can manage connections
- Reserve Delete permissions carefully
Common Permission Scenarios
Operator Role
Typical needs: View data, create charts, monitor systems
- Core → Dashboards: ✓ CRUD
- Core → Chart Composer: ✓ CRUD
- Connectivity → Devices: ✓ Read
- Connectivity → Tags: ✓ Read
- Diagnostics → System: ✓ Read
Engineer Role
Typical needs: Configure devices, manage tags, troubleshoot
- Connectivity → Devices: ✓ CRUD
- Connectivity → Tags: ✓ CRUD
- Connectivity → Poll Groups: ✓ CRUD
- Diagnostics → All: ✓ Read
Viewer Role
Typical needs: View reports, monitor data
- All features: ✓ Read only
- No Create, Update, or Delete permissions
Troubleshooting
Permission changes not visible:
- User must logout and login again
- Permissions refresh on new session
- Clear browser cache if needed
Cannot modify admin permissions:
- This is intentional security feature
- Admin permissions are locked
- Prevents accidental system lockout
User can’t see features:
- Verify correct permissions are checked
- Ensure user logged out/in after change
- Check permission was saved
“Access Denied” errors:
- Check user has correct permissions
- Verify feature permissions include required operation
- Contact administrator to request access
Security Notes
- Permissions checked on every request
- JWT tokens include user ID only (not permissions)
- Permissions loaded fresh from database
- HTTPS prevents token interception
- Session revocation removes access immediately
Related Documentation
- User Management - Creating and managing users
- System Monitoring - Diagnostic tools
